Notice
Recent Posts
Recent Comments
Link
| 일 | 월 | 화 | 수 | 목 | 금 | 토 |
|---|---|---|---|---|---|---|
| 1 | ||||||
| 2 | 3 | 4 | 5 | 6 | 7 | 8 |
| 9 | 10 | 11 | 12 | 13 | 14 | 15 |
| 16 | 17 | 18 | 19 | 20 | 21 | 22 |
| 23 | 24 | 25 | 26 | 27 | 28 |
Tags
- spring integration
- 신재생에너지 발전설비 기사
- 데이터베이스
- write by chatGPT
- 역학
- 유닉스
- jpa
- oracle
- python
- 시스템
- 리눅스
- Database
- chatGPT's answer
- 자바
- 소프트웨어공학
- spring data jpa
- flet
- kotlin
- 인프라
- 파이썬
- 자바네트워크
- 코틀린
- 고전역학
- 자바암호
- 웹 크롤링
- JVM
- write by GPT-4
- Java
- NIO
- GPT-4's answer
Archives
- Today
- Total
기억을 지배하는 기록
Spring Boot+JWT 구현 본문
728x90
Spring Boot 애플리케이션에서 JWT를 사용하여 인증을 처리하는 방법을 보여줍니다. 전체 프로젝트 구성은 다음과 같습니다. 믿고 따라하는 코드
- 프로젝트 구성 및 의존성 추가
- JwtSecurityConfig 클래스 구현
- JwtTokenProvider 클래스 구현
- JwtRequestFilter 클래스 구현
- AlphaUserDetailsServiceImpl클래스 구현
- AuthenticationController 클래스 구현
의존성 추가
먼저, build.gradle 파일에 Spring Security와 JWT 관련 의존성을 추가합니다.
implementation group: 'org.springframework.boot', name: 'spring-boot-starter-web'
implementation 'org.springframework.boot:spring-boot-starter-security'
implementation group: 'io.jsonwebtoken', name: 'jjwt-api', version: '0.11.5'
runtimeOnly group: 'io.jsonwebtoken', name: 'jjwt-impl', version: '0.11.5'
runtimeOnly group: 'io.jsonwebtoken', name: 'jjwt-jackson', version: '0.11.5'
application.properties
jwt.secret=pYaDxnL6wfdxaf4Nq4LjGsr0ObEs4+2IyelhqVzsvGGIruHb9FdndIayVFCg9/LiBOkwI0jSDfOM6JGYp+KXpg==
jwt.expiration=3600
JwtSecurityConfig
이 클래스에서는 인증 및 권한 부여 구성을 정의하고 필요한 필터를 등록합니다.
import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.context.annotation.Bean;
import org.springframework.context.annotation.Configuration;
import org.springframework.security.config.annotation.web.builders.HttpSecurity;
import org.springframework.security.config.annotation.web.configuration.EnableWebSecurity;
import org.springframework.security.config.http.SessionCreationPolicy;
import org.springframework.security.web.SecurityFilterChain;
import org.springframework.security.web.authentication.UsernamePasswordAuthenticationFilter;
import kr.co.thekeytech.batch.web.filter.JwtRequestFilter;
import kr.co.thekeytech.batch.web.security.JwtAuthenticationEntryPoint;
@Configuration
@EnableWebSecurity
public class JwtSecurityConfig {
@Autowired
private JwtAuthenticationEntryPoint jwtAuthenticationEntryPoint;
@Autowired
private JwtRequestFilter jwtRequestFilter;
@Bean
public SecurityFilterChain filterChain(HttpSecurity httpSecurity) throws Exception {
httpSecurity.csrf().disable();
httpSecurity.authorizeHttpRequests().requestMatchers("/login", "/*").permitAll()
.anyRequest().authenticated()
.and().exceptionHandling().authenticationEntryPoint(jwtAuthenticationEntryPoint)
.and().sessionManagement().sessionCreationPolicy(SessionCreationPolicy.STATELESS);
httpSecurity.addFilterBefore(jwtRequestFilter, UsernamePasswordAuthenticationFilter.class);
return httpSecurity.build();
}
}
LoginRequest
REST API 파리미터 객체
import java.io.Serializable;
import lombok.Getter;
import lombok.NoArgsConstructor;
import lombok.Setter;
import lombok.ToString;
@Getter
@Setter
@NoArgsConstructor
@ToString
public class LoginRequest implements Serializable{
private static final long serialVersionUID = 20230403L;
private String username;
private String password;
}
JwtAuthenticationEntryPoint
import java.io.IOException;
import java.io.Serializable;
import org.springframework.security.core.AuthenticationException;
import org.springframework.security.web.AuthenticationEntryPoint;
import org.springframework.stereotype.Component;
import jakarta.servlet.http.HttpServletRequest;
import jakarta.servlet.http.HttpServletResponse;
@Component
public class JwtAuthenticationEntryPoint implements AuthenticationEntryPoint, Serializable {
private static final long serialVersionUID = 20230403L;
@Override
public void commence(HttpServletRequest request, HttpServletResponse response,
AuthenticationException authException) throws IOException {
// 인증 실패 시 401 Unauthorized 에러를 응답합니다.
response.sendError(HttpServletResponse.SC_UNAUTHORIZED, "Unauthorized");
}
}
JwtTokenProvider
JWT 토큰 생성 및 검증 클래스
package kr.co.thekeytech.batch.web.security;
import java.security.Key;
import java.util.Date;
import java.util.HashMap;
import java.util.Map;
import java.util.function.Function;
import org.springframework.beans.factory.annotation.Value;
import org.springframework.security.core.userdetails.UserDetails;
import org.springframework.stereotype.Component;
import io.jsonwebtoken.Claims;
import io.jsonwebtoken.Jwts;
import io.jsonwebtoken.SignatureAlgorithm;
import io.jsonwebtoken.io.Decoders;
import io.jsonwebtoken.security.Keys;
@Component
public class JwtTokenProvider {
@Value("${jwt.expiration}")
private long expiration;
private final Key secretKey;
public JwtTokenProvider(@Value("${jwt.secret}") String secretKey) {
byte[] keyBytes = Decoders.BASE64.decode(secretKey);
this.secretKey = Keys.hmacShaKeyFor(keyBytes);
}
public String generateToken(UserDetails userDetails) {
Map<String, Object> claims = new HashMap<>();
return createToken(claims, userDetails.getUsername());
}
private String createToken(Map<String, Object> claims, String subject) {
return Jwts.builder().setClaims(claims).setSubject(subject)
.setIssuedAt(new Date(System.currentTimeMillis()))
.setExpiration(new Date(System.currentTimeMillis() + expiration * 1000))
.signWith(secretKey,SignatureAlgorithm.HS512)
.compact();
}
public String getUsernameFromToken(String token) {
return getClaimFromToken(token, Claims::getSubject);
}
public Date getExpirationDateFromToken(String token) {
return getClaimFromToken(token, Claims::getExpiration);
}
public <T> T getClaimFromToken(String token, Function<Claims, T> claimsResolver) {
final Claims claims = getAllClaimsFromToken(token);
return claimsResolver.apply(claims);
}
private Claims getAllClaimsFromToken(String token) {
return Jwts.parserBuilder().setSigningKey(secretKey).build().parseClaimsJws(token).getBody();
}
private Boolean isTokenExpired(String token) {
final Date expiration = getExpirationDateFromToken(token);
return expiration.before(new Date());
}
public Boolean validateToken(String token, UserDetails userDetails) {
final String username = getUsernameFromToken(token);
return (username.equals(userDetails.getUsername()) && !isTokenExpired(token));
}
}
JwtRequestFilter
import java.io.IOException;
import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.security.authentication.UsernamePasswordAuthenticationToken;
import org.springframework.security.core.context.SecurityContextHolder;
import org.springframework.security.core.userdetails.UserDetails;
import org.springframework.security.core.userdetails.UserDetailsService;
import org.springframework.security.web.authentication.WebAuthenticationDetailsSource;
import org.springframework.stereotype.Component;
import org.springframework.web.filter.OncePerRequestFilter;
import io.jsonwebtoken.ExpiredJwtException;
import jakarta.servlet.FilterChain;
import jakarta.servlet.ServletException;
import jakarta.servlet.http.HttpServletRequest;
import jakarta.servlet.http.HttpServletResponse;
import kr.co.thekeytech.batch.web.security.JwtTokenProvider;
@Component
public class JwtRequestFilter extends OncePerRequestFilter {
@Autowired
private UserDetailsService userDetailsService;
@Autowired
private JwtTokenProvider jwtTokenProvider;
@Override
protected void doFilterInternal(HttpServletRequest request, HttpServletResponse response, FilterChain chain)
throws ServletException, IOException {
final String requestTokenHeader = request.getHeader("Authorization");
String username = null;
String jwtToken = null;
if (requestTokenHeader != null && requestTokenHeader.startsWith("Bearer ")) {
jwtToken = requestTokenHeader.substring(7);
try {
username = jwtTokenProvider.getUsernameFromToken(jwtToken);
} catch (IllegalArgumentException e) {
System.out.println("Unable to get JWT Token");
} catch (ExpiredJwtException e) {
System.out.println("JWT Token has expired");
}
} else {
logger.warn("JWT Token does not begin with Bearer String");
}
if (username != null && SecurityContextHolder.getContext().getAuthentication() == null) {
UserDetails userDetails = this.userDetailsService.loadUserByUsername(username);
if (jwtTokenProvider.validateToken(jwtToken, userDetails)) {
UsernamePasswordAuthenticationToken usernamePasswordAuthenticationToken = new UsernamePasswordAuthenticationToken(
userDetails, null, userDetails.getAuthorities());
usernamePasswordAuthenticationToken
.setDetails(new WebAuthenticationDetailsSource().buildDetails(request));
SecurityContextHolder.getContext().setAuthentication(usernamePasswordAuthenticationToken);
}
}
chain.doFilter(request, response);
}
}
AlphaUserDetailsService
import java.util.Map;
import org.springframework.security.core.userdetails.UserDetails;
import org.springframework.security.core.userdetails.UserDetailsService;
public interface AlphaUserDetailsService extends UserDetailsService {
public Map<String, UserDetails> getUsers();
}
AlphaUserDetailsServiceImpl
import java.util.HashMap;
import java.util.Map;
import org.springframework.security.core.userdetails.User;
import org.springframework.security.core.userdetails.UserDetails;
import org.springframework.security.core.userdetails.UsernameNotFoundException;
import org.springframework.stereotype.Service;
@Service
public class AlphaUserDetailsServiceImpl implements AlphaUserDetailsService {
//테스트용 사용자 정보
private Map<String, UserDetails> users = new HashMap<>();
public AlphaUserDetailsServiceImpl() {
// Create a sample user
UserDetails user = User.withUsername("admin")
.password("{noop}password")
.roles("ADMIN")
.build();
users.put("admin", user);
}
@Override
public UserDetails loadUserByUsername(String username) throws UsernameNotFoundException {
UserDetails user = users.get(username);
if (user == null) {
throw new UsernameNotFoundException("User not found");
}
return user;
}
public Map<String, UserDetails> getUsers() {
return users;
}
}
AuthenticationController
import java.util.HashMap;
import java.util.Map;
import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.http.ResponseEntity;
import org.springframework.security.core.userdetails.UserDetails;
import org.springframework.web.bind.annotation.GetMapping;
import org.springframework.web.bind.annotation.PostMapping;
import org.springframework.web.bind.annotation.RequestBody;
import org.springframework.web.bind.annotation.RestController;
import kr.co.thekeytech.batch.web.model.LoginRequest;
import kr.co.thekeytech.batch.web.security.JwtTokenProvider;
import kr.co.thekeytech.batch.web.service.AlphaUserDetailsService;
@RestController
public class AuthenticationController {
@Autowired
private AlphaUserDetailsService alphaUserDetailsService;
@Autowired
private JwtTokenProvider jwtTokenProvider;
@PostMapping("/login")
public ResponseEntity<?> authenticateUser(@RequestBody LoginRequest loginRequest) {
final UserDetails userDetails = alphaUserDetailsService.loadUserByUsername(loginRequest.getUsername());
String jwt = jwtTokenProvider.generateToken(userDetails);
Map<String, String> response = new HashMap<>();
response.put("token", jwt);
return ResponseEntity.ok(response);
}
@GetMapping("/users")
public ResponseEntity<Map<String, UserDetails>> getUserList() {
return ResponseEntity.ok(alphaUserDetailsService.getUsers());
}
}
POSTMAN: POST /login 테스트
LoginRequest 구조에 맞춰 json 파라미터 전달
응답된 token을 다음 요청부터는 Header에 넣어서 전달 해야 함.
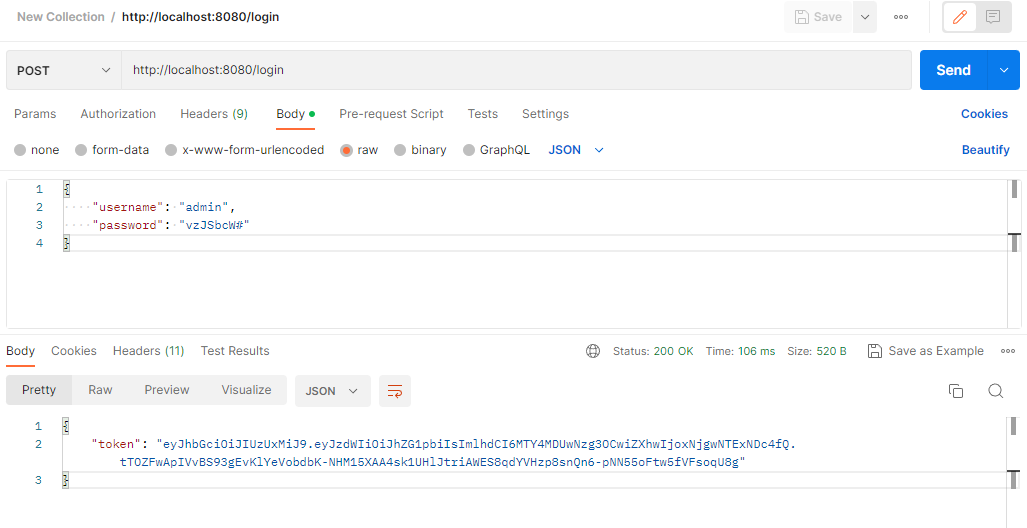
POSTMAN: GET /users 테스트

728x90
'Spring.io' 카테고리의 다른 글
| Spring Batch에서 REST API로 Quartz Scheduler 변경하기 (0) | 2023.04.04 |
|---|---|
| Spring Batch Job을 REST API로 실행하기 (0) | 2023.04.04 |
| Spring Boot+WebSocket 구현 (0) | 2023.03.31 |
| Spring Batch+quartz 연동 (0) | 2023.03.31 |
| Spring Boot Actuator (0) | 2023.03.23 |
Comments





